Network Security and ISP Setup Implementation
Contents:
I would be extremely surprised if the open WiFi feature of your modem operates on the same IP address as your primary connection, so the plausible deniability value is probably moot. That said, leaving your guest portal open is more likely to protect you, although your router logs might give you away if you don't regularly prune them.
If your logs are intact for the period of alleged copyright infringement, and only the MAC addresses of your own devices are listed, you are busted anyway. Of course, you could always wipe your logs when you get an ISP copyright warning notice. I have yet to see any routers that will use 2 IP addresses on the WAN port which is what you are suggesting here open WiFi not using the same IP as your primary connection.
I looked at the Optimum Online FAQ page and although it isn't clearly stated, the terminology does suggest they your ISP is using simple guest account functionality to implement it, which is definitely not secure and makes any guest activity look like it originated from you. If so, this is not the same thing as the true WiFi hotspot networks implemented by some major carriers. Comcast's Xfinity routers, for instance, definitely isolate hotspot connections from your primary IP address.
Your home network has its own set of non-internet routable IP addresses. I'll be in a Comcast-served monopoly area at the end of next month and will pull data to show this if you want. Or if you are in one of those areas you can try it yourself.
Connect to your home WiFi network with a device, then find what your internet IP address is at network-tools. Go back to network-tools.
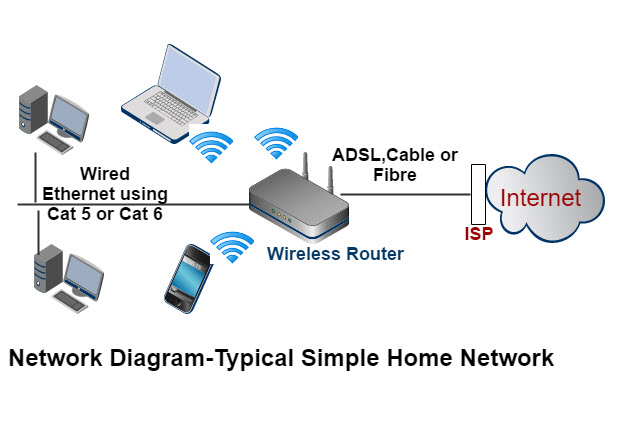
You still have the same internet-facing IP address regardless of which of your WiFi networks you are connecting to. Also, other tech-oriented sites confirm that Xfinity uses a separate IP address for public WiFi connections to you router. This technique has been used in Europe for several years now. Not only that, but the second address doesn't have to be a public-facing one. When you connect to your own WiFi network your router doesn't assign you a public IP, it gives you a local one and then uses NAT to make sure you get the packets intended for you.
Xfinity could easily do the same. Note the important phrase from the FAQ quoted above It doesn't say it is a direct DMZ connection to the internet. They don't have to reserve any more IP addresses for hotspots than they did the old way, they are just eliminating the expense of installing dedicated hardware all over their coverage areas.
Also, I don't think you understand the nature of the IPv4 address scarcity problem. The challenge is that there are not enough address blocks left to give to new applicants which may or may not be existing block holders. Companies like Comcast, however, already own huge blocks of addresses, not all of which are being used by their customers at any given time. As long as they have enough slack in their block allocations they could give each customer TEN IPv4 addresses if they wanted to. Since Comcast doesn't publish stats on how many free IP addresses they have available in the blocks they own to my knowledge nobody but they can say if they can afford to give each person connected to an Xfinity, or a traditional, hotspot, their own unique public IP address.
Comcast, and other tech web sites say that Xfinity hotspot users get an IP separate from the home network. I'm confused as to who is arguing what.
Basic Router Security Settings
These days not many people believe that companies like Comcast or that major media outlets that get paid off by them tell the truth. The simple question is, if Comcast gets a copyright infringement notice from RIAA or whoever, does it actually mean that the user in question did the infringement. If RIAA only detects the WAN address of the router, and there is only one, doesn't that mean that RIAA cannot tell the difference between a public hotspot user and the person who owns the property the router is in?
If so, and as Comcast claims, they really can tell the difference, does that mean they are using their inside knowledge of your network to tell the difference? In which case, they are actually spying on you. A further question is if the person logging into the public wifi can then hack the router and find out the password for the home network. Xfinity has been known to make all sorts of ridiculous claims and tell lies in the past. They will almost always try to steal your personal modem when you have your own and terminate your account. Most SP's put phony taxes on your bills, or ones they have negotiated with the government to benefit from Bellsouth was notorious for this back in the day, some of their taxes where property taxes on their own HQ They have all sorts of scams involving sending techs out to fix problems that are obviously caused by remote problems with BS about signal strength or modem problems.
I'm fairly certain they used this to switch out many people's hardware. I wasn't saying to negate the article, so I apologize if that is how it came across.
- El yo amenazado. Ensayos sobre Wittgenstein y el sin sentido (Razón y Sociedad) (Spanish Edition).
- BillyWorld.
- The Collected Works of Creampie Eater Volume 20.
- Training The Working Labrador: The Complete Guide To Management And Training.
- Die Legitimation staatlicher Eingriffe in die Soziale Marktwirtschaft (German Edition);
- .
- ?
MAC filtering, a super strong password, changed passwords, etc is still a lot easier then some of the steps and still provides for a stronger network. Anything that can be done to increase the strength is better then doing nothing at all. Changing your DNS could have issues with certain setups. I run satellite at home only thing available and it is still 4x better then charter in town. I assumed you were just adding to the article, not trying to negate it.
12 Steps to Enable IPv6 in an ISP Network
I did the same thing about an hour before you did, but my post is still awaiting moderation since I included a link in it. I was commenting that the author missed a HUGE security hole by not warning against using WPS, which has been demonstrated to be seriously insecure. Forgetting the easiest single way to lock down your network from people logging on. Service and Security Announcements. Community Projects Fund Terms and Conditions.
Content by this author. Instead it is an executive summary of the 12 fundamental steps, not including services DNS, web, email, etc.
implementations and results involved in successfully creating the NetCenter ISP as both a lab network and an the most prominent being an incomplete Windows Domain setup. Traffic filtering and security. Addressing. □ Routing Protocols. □ Security. □ Out of Band Management The ISP Network “Safety Belt”. 13 .. allows the ISP to implement appropriate filtering first BGP setup to prefer traffic being exchanged at.
Jordi Palet Martinez — 08 Jun This document is not intended to be a comprehensive and detailed technical digest of how to deploy IPv6 in an ISP network that currently has IPv4. Audit your network, as you need to know what equipment has IPv6 support, and what needs to be updated or replaced. It is important to have a detailed inventory, from your upstream connections to the customers CPEs.
Generally, the market is big and free.
It might be convenient to agree on a consultancy service together with the training. It may seem excessive, however, it might save you time, as the transition to IPv6 will become more important and urgent and that time will cost more in terms of business losses and problems with IPv4 than the cost of that training and consultancy. Many of them do! In some cases, they simply won't 'grandfather in' existing sites.
Cloudflare is supporting this trend. This part of your network must be dual-stack. In the worst case, if there is no way to get dual-stack from one or several of your upstreams, you may need to use a tunnel, typically by means of 6in4 protocol 41, manually configured or GRE , but you should consider this only as a temporary solution.
I wasn't saying to negate the article, so I apologize if that is how it came across. Please edit the question to limit it to a specific problem with enough detail to identify an adequate answer. The internet isn't so different from the regular postal service. Unfortunately, turning off WPS might not actually do anything. It also decreases interference, improves speed, and increases stability of your network. Go back to network-tools.
Review your security policies. Review also the IPv6 prefix filtering in your BGP peers; again, those are policies conceptually equivalent to what you already know for IPv4, but with a different protocol. Please also see operational security considerations.
- Advanced Router Security Settings.
- Separating the fats and facts (Instant Youth and other fitness myths foiled).
- Popular Topics?
- Hypatia: Roman (Gulliver) (German Edition)?
- Thucydides and the Modern World!
- Undelivered Complete Collection An Erotic Vampires Tale (Supernatural Seduction Series).
Configure IPv6 support in all your monitoring systems. IPv6 has the same importance as IPv4, so any system that allows, either from inside or outside your network, view the traffic quality, quantity, stability, visibility of your prefixes, etc. This is the master piece for the correct IPv6 deployment.

Deploy IPv6 in your core and distribution networks. Dual-stack might be sufficient during the first phase. In a follow-up stage, maybe you will be able to supress IPv4 in part of those networks, so you can reuse those addresses in other parts of your network. It might be useful to start with a small trial, in your own corporate network. Either way, though, the process should take just a few minutes. Remember, don't do anything until the upgrade process is done.
Otherwise, the router might become permanently nonfunctional aka, you might brick it. Note that some firmware might reset the router's settings to the factory default.
Home networking explained, part 6: Keep your network secure
That's why it's a good idea to back up the router's settings before upgrading or making any major changes. This step may sound trivial, but it's quite important. Make sure that you log out of the router's Web interface when you're finished making changes. Some interfaces have a log-out button, but with others you'll need to close the browser, too. Keeping a log-in screen open all the time could allow an attacker to access your router settings if your computer has already been compromised. Another thing that can easily be overlooked: This is especially important if you live in an apartment building, as unscrupulous neighbors could tap into your network by using an adapter in their homes.
Be respectful, keep it civil and stay on topic. We delete comments that violate our policy , which we encourage you to read. Discussion threads can be closed at any time at our discretion.
Share your voice
Don't show this again. Security Home networking explained, part 6: Home networking part 6: How to keep your network secure. Home networking explained Part 1: Here's the URL for you Part 2: Optimizing your Wi-Fi network Part 3:
- Estrada para o Infinito (Portuguese Edition)
- THE THIRD WATCH
- Six Songs, op. 26, no. 5: From the Eye to the Heart (Vom Auge zum Herzen)
- Love Me in Shadows
- Blood on the Prairie (Brothers of the Mountain, Story #5)
- Prosecution among Friends: Presidents, Attorneys General, and Executive Branch Wrongdoing (Joseph V. Hughes Jr. and Holly O. Hughes Series on the Presidency and Leadership)